Permissions
The actions a client session can take in Diffusion™ Cloud are controlled by a set of permissions. These permissions are assigned to roles.
- Path
- Permissions at path scope apply to actions on a topic path, request-response message path
or session lock name.
Path-scoped permissions are defined against paths. The permissions that apply are the set of permissions defined at the most specific path.
- Global
- Permissions at global scope apply to actions on Diffusion Cloud .
Path permissions
The path-scoped permissions are listed in the following table:
| Name | Description |
|---|---|
| Acquire a session lock. The names of the locks that can be acquired are restricted to the paths of the permission scope. | |
| Use a topic selector that selects the topic path. A session must have this permission for any topic selector used to subscribe or fetch. | |
| Grant read access to the topics. If a session does not have this permission for a topic, that topic does not match subscriptions and is excluded from fetch requests. Also, the topic's details cannot be retrieved. Changes to the security store which alter permission assignments are applied dynamically. This means that if you change the permissions granted by a role, the new configuration is immediately applied to all sessions. Each session's topic selections are re-evaluated with the new permissions, and subscriptions are added or removed accordingly. |
|
| Evaluate a query on a time series topic that can potentially return a non-current view of all or part of a time series. Such queries include value range queries that specify an edit range, and all types of edit range query. Evaluating a query also requires . | |
| Submit edit events to a time series topic. Updating a time series topic also requires . | |
| Submit edit events to a time series topic where the event author is the same as the principal of the calling session. Updating a time series topic also requires . | |
| Update topics at or below a topic branch. | |
| Create or remove topics at or below a topic branch. | |
| Send a message to Diffusion Cloud through a message path. | |
| Send a message to a client session through a message path. | |
|
Expose a branch of the topic tree as a virtual session tree. The is powerful, since it allows a session to expose a whole branch of the topic tree under a different set of path permissions. A session granted for a particular path effectively has the permission for all descendant paths. From a security perspective, if a role grants at branch X it is ineffectual for it also to deny at a child branch X/Y because a branch mapping to X can still expose paths below X/Y. |
Configuring path permissions
You can configure path permissions using the client API or using the Security tab after logging in to Diffusion Cloud.
Understanding path permissions
Path permissions enable you to control access to resources that have a path-based hierarchy. The most common example is the topic tree, but request-response messaging paths and session lock names also use path permissions.
A session can carry out an action on a resource if any of its roles grants the appropriate permission for the resource path.
Each role assigns parts of the path hierarchy to permissions. The permissions a role grants for a path are determined by the assignment with the longest prefix of the path. For a given role, only one assignment applies to a path.
- permission for the topic path telemetry/gps
- and permission for the path telemetry/gps/ships
Consider the topic telemetry/gps/submarines/nautilus. Only the first rule matches the path, so the session would have permission for the topic.
Consider the topic telemetry/gps/ships/titanic. Both rules match, but the second rule is more specific, so the session has both and permission.
A session has a permission if any of its assigned roles has that permission (or includes a role that has that permission).
You can also define default path permissions. These are used if there are no matching path permissions and the path is not isolated (see below).
The path permissions included in the set of roles that are predefined in Diffusion Cloud are all scoped to the whole path hierarchy.
Isolating branches of the path hierarchy
Normally, if a role has no permission assignment for a path, the permissions are inherited from the permission assignment for the longest prefix of the path.
For example, if a role has no permission assigned for telemetry/gps/balloons, but it does have one for telemetry/gps, telemetry/gps/balloons will normally inherit the permissions.
Sometimes you may not want this inheritance to apply to a particular branch. For example, suppose your topic tree has this branch, with sensitive data that should only be accessed by sessions with a special role:
telemetry/gps/ships/glomar-explorer
If you grant another role permission to telemetry/gps/, sessions with that role will be able to read the sensitive branch.
One workaround would be to avoid creating any path permissions above telemetry/gps/ships/, but that means creating many more specific path permissions and updating them every time a new ship is added.
Isolating paths is a way to disable the usual inheritance rules and ignore default path permissions.
You can use the client API or the management console to create a rule that isolates a specified path.
In the above example, suppose you isolate telemetry/gps/ships/glomar-explorer. Now a role that has permission to telemetry/gps/ will not grant the ability to read the glomar-explorer topic or any of its children, such as telemetry/gps/ships/glomar-explorer/location.
In addition, a default path permission granting does not apply to the isolated path.
Path scope example
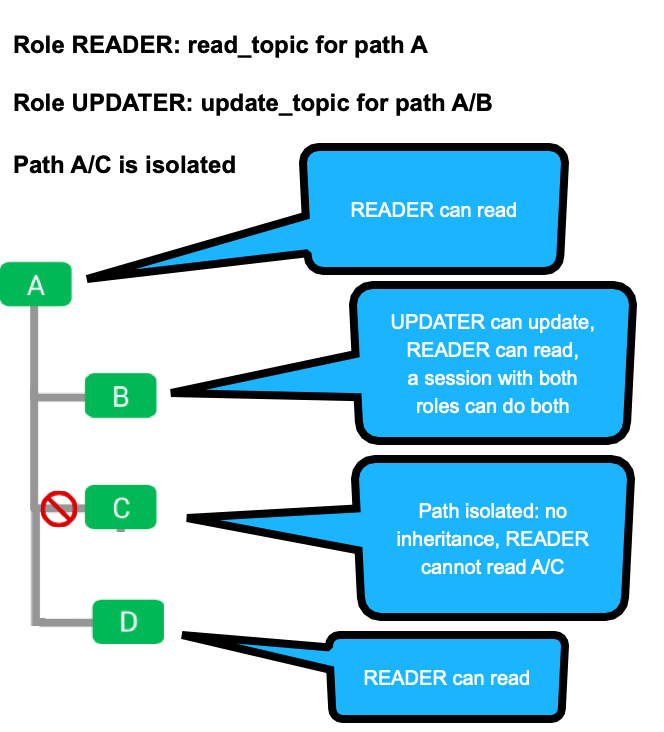
This example demonstrates how path permissions and isolated paths combine.
-
The READER role has read_topic permission for path A, so a session with just this role can read the content of topic A. It can also read A/B and A/D, because the first part of the path matches and there are no conflicting permission rules.
-
The UPDATER role has update_topic permission for path A/B only.
-
A session with both READER and UPDATER roles combines the permissions above, granting read_update and update_topic permissions for A/B, as well as read access to A and A/D.
Note that if you had used a single role and granted read_update to A and update_topic to A/B, the session would not have both permissions to A/B, because only the more specific rule would be applied.
-
The path A/C is isolated, so normal inheritance rules do not apply. The READER role cannot read A/C (or any child topics like A/C/E).
set "READER" path "A" permissions [READ_TOPIC] set "UPDATER path "A/B" permissions [UPDATE_TOPIC] isolate path "A/C"
See DSL syntax: security store for details.
Understanding the and permissions
The default configuration grants the and permissions to CLIENT sessions including anonymous sessions. You can alter this configuration to protect sensitive topics.
To fetch or subscribe using a topic selector, a session must have permission for each individual path that the selector may match. This allows to be granted to a branch of the topic tree and explicitly revoked for specific sub-branches.
For full path pattern topic selectors, the model is even more restrictive: permission is required for all paths, at and below the path prefix of the selector. This is necessary to prevent circumvention using advanced regular expressions.
When the subscription or fetch request completes, the resulting topics are further filtered based on the permission.
A session that has but not for a particular topic path cannot subscribe directly to topics belonging to the path. However, the session can be independently subscribed by a control session that has permission in addition to the appropriate permission.
Managing all subscriptions from a separate control session
You can prevent client sessions from subscribing themselves to topics and control all subscriptions from a separate control client session that uses SubscriptionControl feature to subscribe clients to topics.
To restrict subscription capability to control sessions, configure the following permissions:
- Grant the permission
- Grant the permission
This can either be granted for the default path scope or more selectively to restrict the topic selectors the control session can use.
- Grant to the appropriate topics.
- Deny the permission by
default.
Do not assign the session a role that has the permission for the default path scope. This prevents the session from subscribing to all topics using a wildcard selector.
- Optionally, grant the permission to specific branches of the topic tree to which the session can subscribe freely.
Global permissions
The global permissions are listed in the following table:
| Name | Description |
|---|---|
| List or listen to client sessions. | |
Alter a client session. This covers a range of actions including the following:
|
|
| Register any handler with Diffusion Cloud . | |
| Register an authenticator. The permission is also required to perform this action. |
|
Server control functions:
|
|
| View the security policy. | |
| Change the security policy. | |
| View the topic views. | |
| Change the topic views. To add a new topic view the session also needs the select_topic permission for the prefix of the source selector of the topic view being added. |